External Vault Integration (Enterprise feature)
For users already using external vault services, Insomnia now supports integration with the following vault service providers:
By integration with external vaults, Insomnia will retrieve the secret values from the external vault automatically when sending requests.
AWS Secrets Manager
AWS Secrets Manager is a service that securely stores, manages, and retrieves sensitive data.
Once integrated with AWS Secrets Manager in Insomnia, you can link environment variables to secrets stored in AWS Secrets Manager and automatically retrieve them when sending requests.
- Navigate to the Preferences page and select the Cloud Credentials tab. Click Add Credentials, choose AWS.
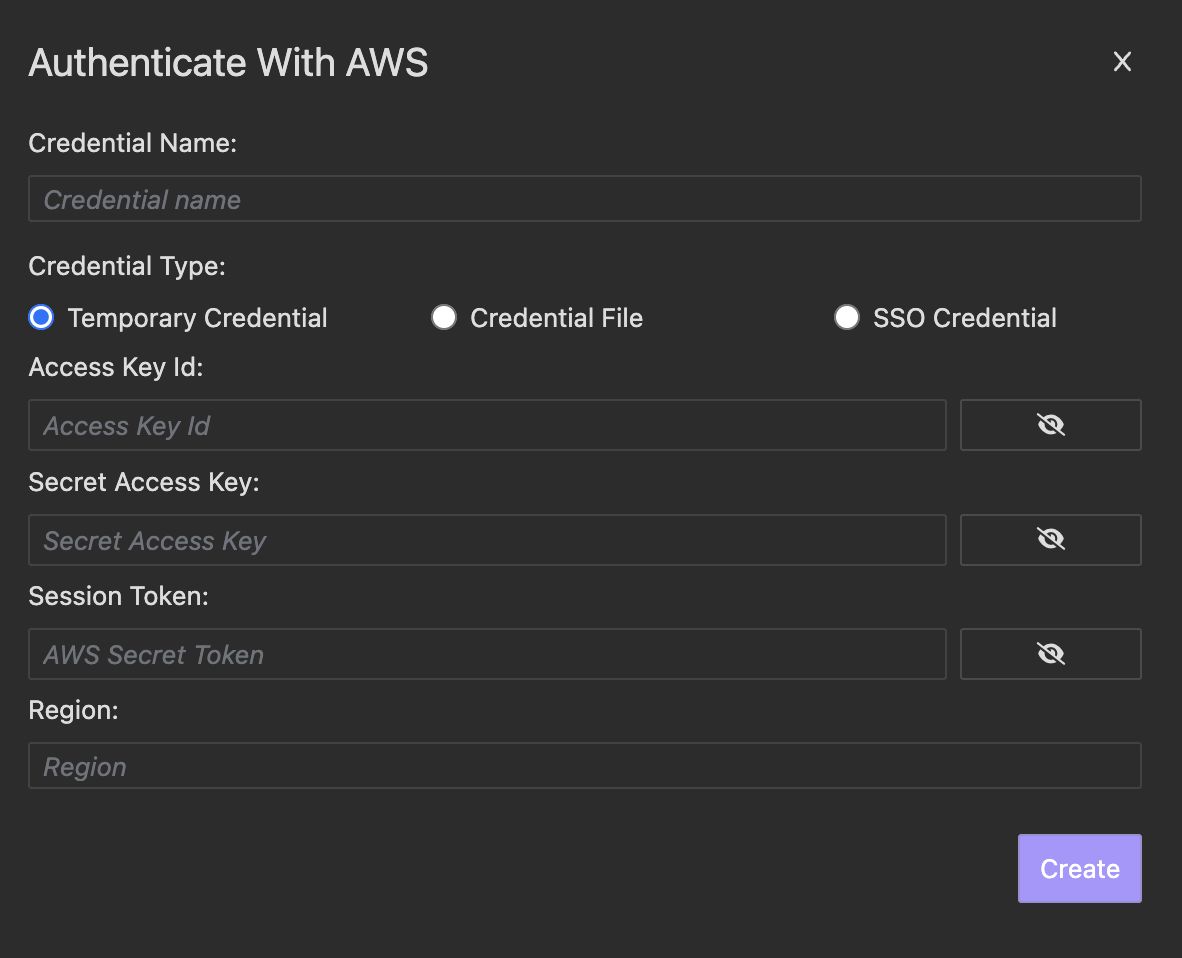
- For temporary security credentials, choose Temporary Credential and enter your credentials.
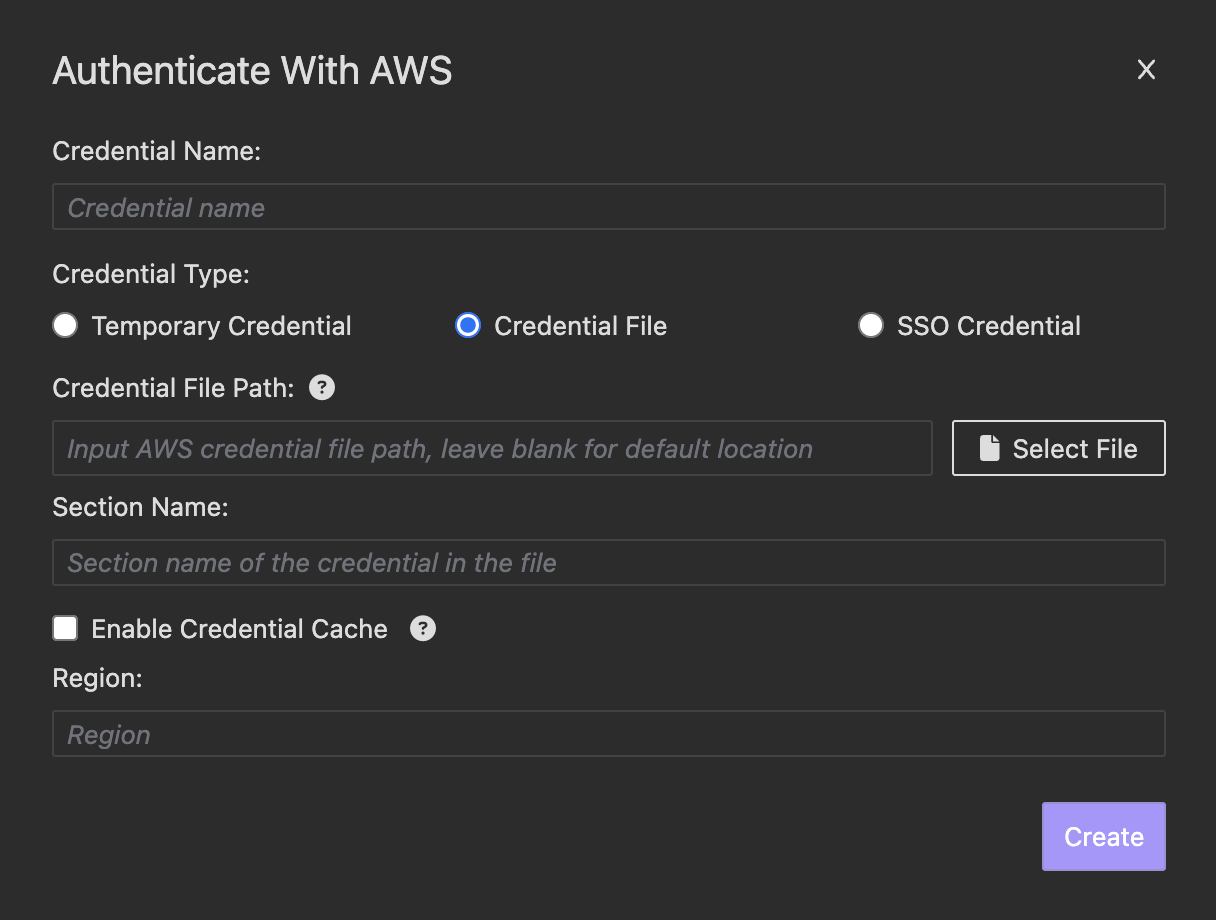
- For file credential generated by CLI, choose Credential File and enter your credential file path and credential section name.
-
For SSO credential generated by AWS CLI, choose SSO Credential and enter your config file path, profile name and credential file path
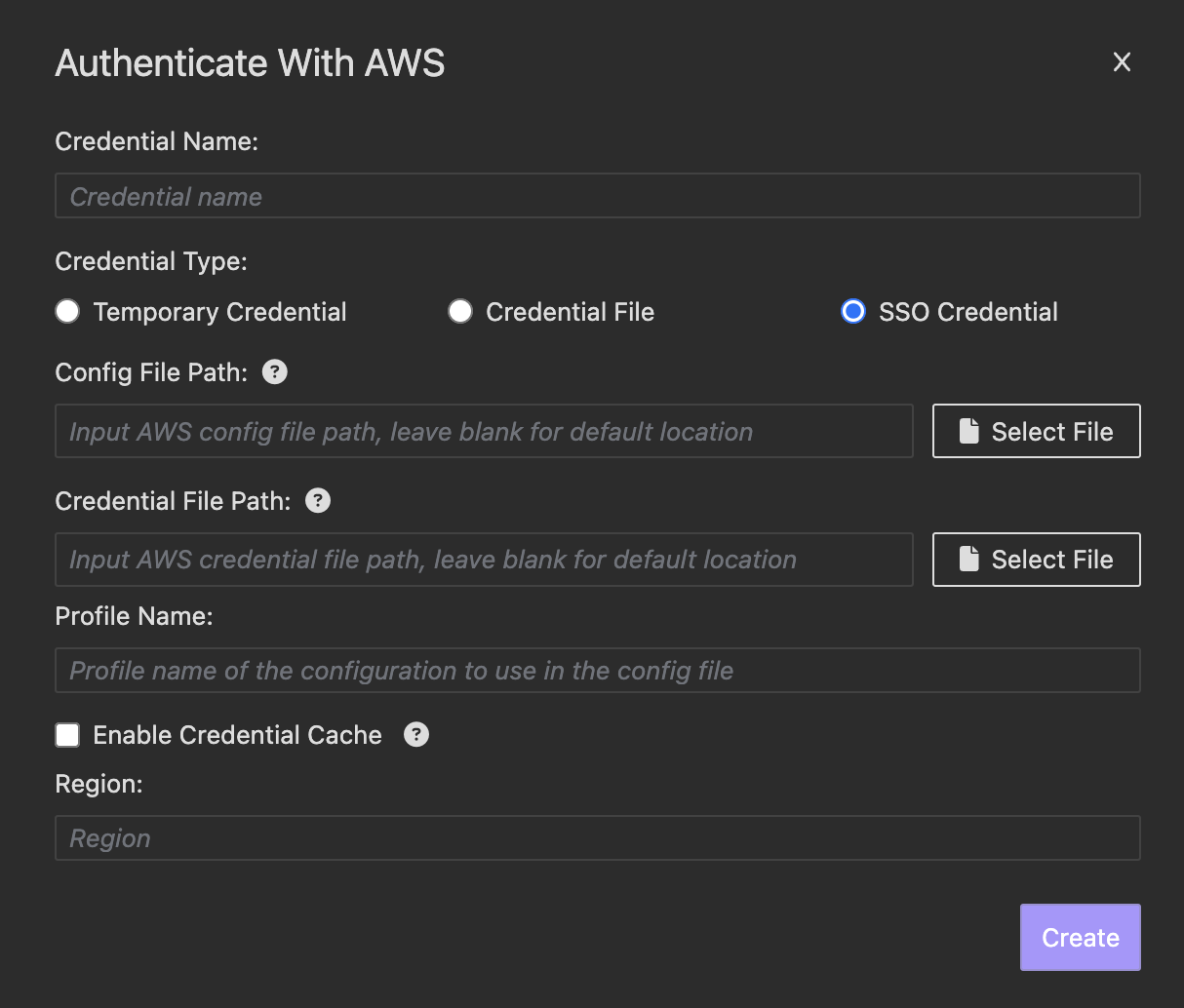
Note: Enable Credential Cache will cache the file content in memory. If your file credential or SSO credential are expected to change, uncheck this option to ensure the latest file content is always loaded.
- For temporary security credentials, choose Temporary Credential and enter your credentials.
- Open the AWS Secrets Manager from the context menu.
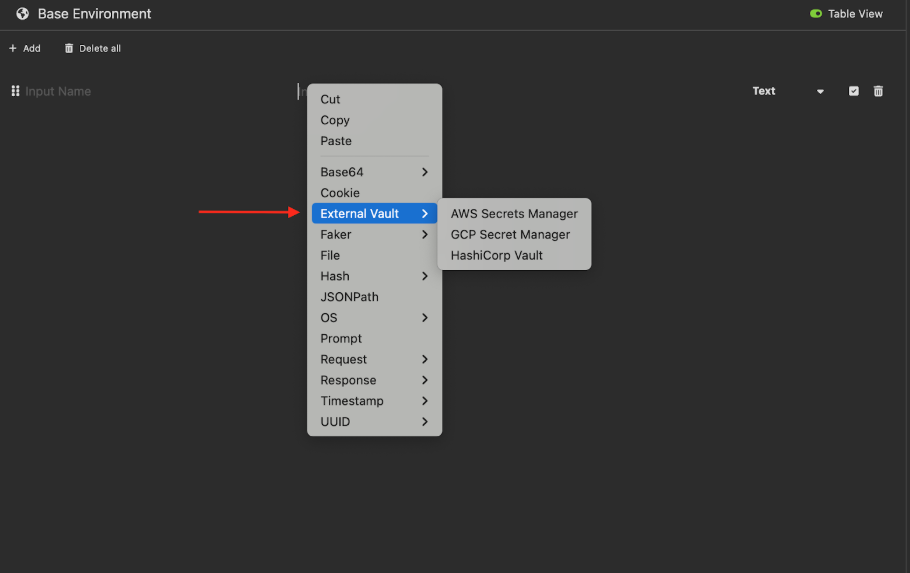
- Fill the information needed for retrieving the secrets, like
secret name,secret versionandsecret type
GCP Secret Manager
GCP Secret Manager is a service that securely stores, manages, and retrieves sensitive data.
Once integrated with GCP Secret Manager in Insomnia, you can link environment variables to secrets stored in GCP Secret Manager and automatically retrieve them when sending requests.
- Navigate to the Preferences page and select the Cloud Credentials tab. Click Add Credentials, choose GCP, and select your local service account key file to authenticate with GCP.
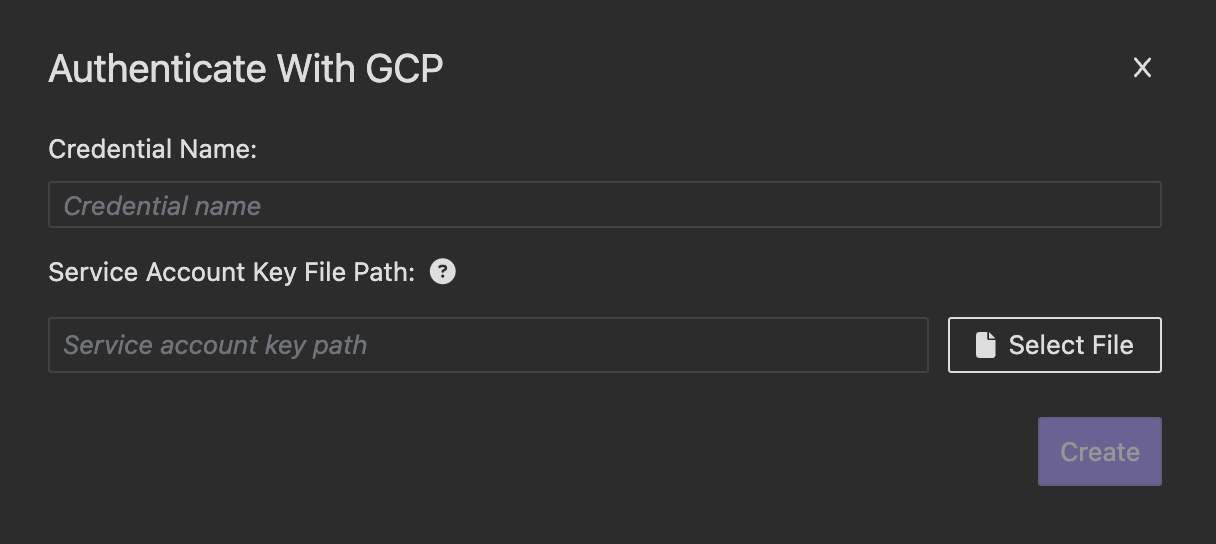
- Open the GCP Secrets Manager from the context menu.

- Fill the information needed for retrieving the secrets, like
secret nameandsecret version.
HashiCorp Vault
HashiCorp Vault is a service that securely stores, manages, and retrieves sensitive data.
Once integrated with HashiCorp Vault in Insomnia, you can link environment variables to secrets stored in HashiCorp Vault and automatically retrieve them when sending requests.
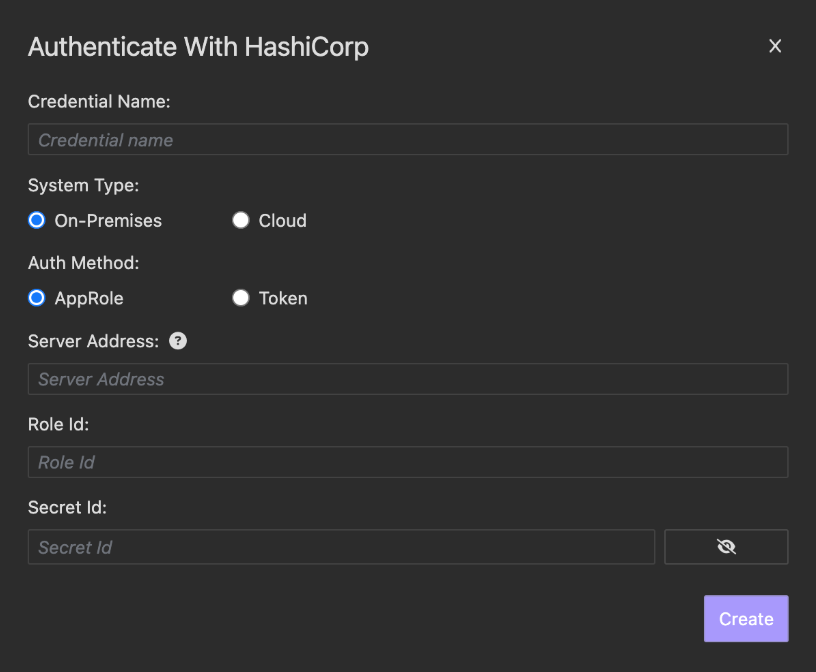
- Navigate to the Preferences page and select the Cloud Credentials tab. Click Add Credentials, choose HashiCorp, and enter your credentials.
-
For HashiCorp vault server environment choose On-Premises. You can input either AppRole or Token for authentication.
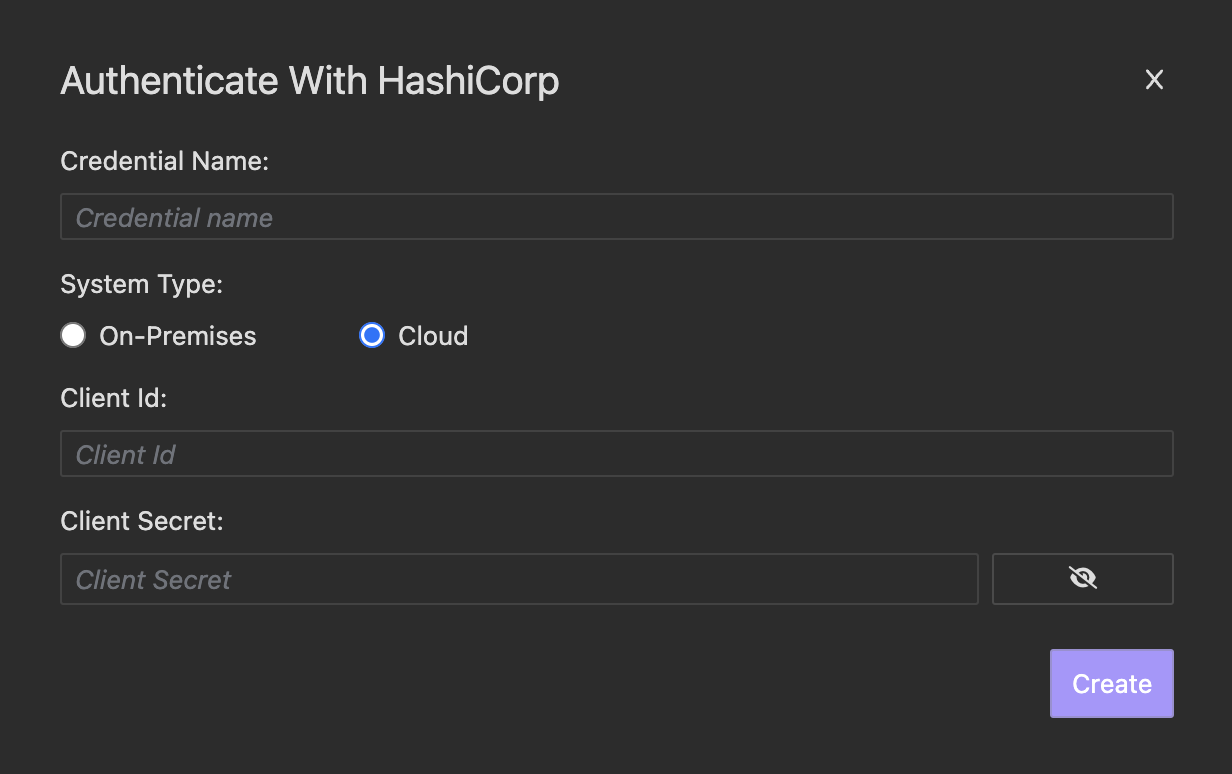
- For HashiCorp cloud vault environment choose Cloud. You should input the service principal Client Id and Client Secret.
- Open the HashiCorp Vault from the context menu.

-
When filling the information needed, we will show different config form based on the HashiCorp environment.
For cloud environment, filling the information needed:
input Organization Id,Project Id,App Name,Version and Secret Name.For vault server environment, Insomnia supports retrieving secrets from KV secret engine for version v1 & v2, so users must choose the
secret engine versionthen filling the information.
Azure Key Vault
Azure Key Vault is a service that securely stores, manages, and retrieves sensitive data.
Once integrated with Azure Key Vault in Insomnia, you can link environment variables to secrets stored in Azure Key Vault and automatically retrieve them when sending requests.
- Navigate to the Preferences page and select the Cloud Credentials tab. Click Add Credentials, choose Azure.
- You will be redirected to your browser to authorize Insomnia to access your Azure account. After authorization, you will be redirected back to Insomnia, where a new credential will be added. The credential’s name will be your Azure account username.
- Open the Azure Key Vault from the context menu.

- Fill the information needed for retrieving the secrets, like
Secret Identifier.
External Vault Secrets Cache Mechanism
By default, all secrets retrieved from cloud vault services are stored in memory for 30 minutes. Insomnia will automatically fetch the secret again if the cache expires or does not exist. Users can configure the cache duration and manually reset the cache in the Cloud Credentials tab within the Preferences page.
External Vault Integration In Inso CLI
Inso CLI allows you to use Insomnia application functionality in your terminal and CI/CD environments for automation.
If you want to run collection command with external vault integration in CI/CD pipelines, you need to expose extra environment variables for authentication purpose.
Here’s the list of environment variables needed for different cloud service providers:
AWS
- Temporary security credentials
INSOMNIA_AWS_TYPE = 'temporary'
INSOMNIA_AWS_ACCESSKEYID = <Access Key ID >
INSOMNIA_AWS_SECRETACCESSKEY = <Secret Access Key>
INSOMNIA_AWS_SESSIONTOKEN = <Session Token>
INSOMNIA_AWS_REGION = <AWS Resource Region>
- Credential File
INSOMNIA_AWS_TYPE = 'file'
INSOMNIA_AWS_SECTION = <Section Name In AWS Credential File>
INSOMNIA_AWS_FILEPATH = <AWS Credential File Path> (Optional)
INSOMNIA_AWS_ENABLECACHE = <Option To Enable File Cache> (Optional)
INSOMNIA_AWS_REGION = <AWS Resource Region>
- SSO Credential
INSOMNIA_AWS_TYPE = 'sso'
INSOMNIA_AWS_SECTION = <Profile Name In AWS Config File>
INSOMNIA_AWS_CONFIGFILEPATH = <AWS Config File Path> (Optional)
INSOMNIA_AWS_FILEPATH = <AWS Credential File Path> (Optional)
INSOMNIA_AWS_ENABLECACHE = <Option To Enable File Cache> (Optional)
INSOMNIA_AWS_REGION = <AWS Resource Region>
GCP
INSOMNIA_GCP_SERVICEACCOUNTKEYFILEPATH = <GCP Service Account Key File Path>
HashiCorp
- Hashicorp Cloud Platform
INSOMNIA_HASHICORP_TYPE = 'cloud'
INSOMNIA_HASHICORP_CLIENT_ID = <HCP Service Principal Client Id>
INSOMNIA_HASHICORP_CLIENT_SECRET = <HCP Service Principal Client Secret>
- HashiCorp Vault Server
-
App Role
INSOMNIA_HASHICORP_TYPE = 'onPrem' INSOMNIA_HASHICORP_AUTHMETHOD = 'appRole' INSOMNIA_HASHICORP_SERVERADDRESS = <Hashicorp Vault Server Address> INSOMNIA_HASHICORP_ROLE_ID = <Hashicorp Vault Server App Role ID> INSOMNIA_HASHICORP_SECRET_ID = <Hashicorp Vault Server App Role Secret ID> -
Token
INSOMNIA_HASHICORP_TYPE = 'onPrem' INSOMNIA_HASHICORP_AUTHMETHOD = 'token' INSOMNIA_HASHICORP_SERVERADDRESS = <Hashicorp Vault Server Address> INSOMNIA_HASHICORP_ACCESS_TOKEN = <Hashicorp Vault Server Access Token>
-